7 Essential Tips for Protecting Internal Messages: The Ultimate Guide to Secure Team Communication
Protecting internal messages might sound like a job for a spy movie hero — but guess what? It’s actually your job now. In today’s digital jungle, you’re juggling loads of sensitive info, and keeping it safe isn’t just nice to have… it’s non-negotiable.
Let’s be honest: hackers don’t take coffee breaks, and your unprotected messages are their happy hour. That’s why you need to step up your secure communication game, before your emails become the next season of “Hacked and Exposed.”
But don’t panic — I’ve got your back. In this guide, we’ll walk (not run) through how to lock down your internal chats, train your team without boring them to tears, and avoid ending up in your company’s next security incident post-mortem. Ready? Let’s protect those messages like a pro
Protecting Your Internal Messages: A Smart Communication Strategy
Table of Contents
Key Takeaways
- Understand the importance of protecting internal messages.
- Learn about the risks associated with unsecured digital communication.
- Discover best practices for secure internal communication.
- Implement robust security measures to safeguard your organization’s information.
- Stay ahead of cyber threats with up-to-date security practices.
The Growing Importance of Message Protection
With the rise in cyber threats, message protection has emerged as a crucial aspect of business security. As you navigate the complexities of modern workplace communication, ensuring the privacy and security of your internal messages is vital.
1. Current Threats to Business Communications
Businesses today face a myriad of threats to their communications, from phishing attacks to sophisticated malware. Phishing attacks, in particular, have become more targeted, making it easier for attackers to deceive employees into divulging sensitive information.
2. The Real Cost of Data Breaches
The financial impact of a data breach can be devastating. According to recent studies, the average cost of a data breach is around $4.35 million. This includes costs associated with notification, remediation, and lost business opportunities.
| Cost Category | Average Cost |
| Notification Costs | $0.5 million |
| Remediation Costs | $1.2 million |
| Lost Business Opportunities | $2.65 million |
Protecting your internal messages is not just about avoiding financial loss; it’s also about maintaining trust with your clients and stakeholders. By prioritizing data privacy and workplace communication security, you can safeguard your business against the growing threats in the digital landscape.
Understanding Communication Vulnerabilities
With the rise in digital communication, your internal messaging platforms have become a prime target for cyber threats. As you rely more heavily on internal communication software, understanding the vulnerabilities in your communication systems is crucial.
1. Common Attack Vectors in Workplace Communication
Cyber attackers often exploit weaknesses in workplace communication to gain unauthorized access to sensitive information. Common attack vectors include phishing emails, malware-infected attachments, and vulnerable software updates. To protect your internal communication channels, it’s essential to be aware of these threats and implement robust security measures.
2. Insider Threats vs. External Threats
Threats to your internal communication software can come from both inside and outside your organization. Insider threats may arise from employees intentionally or unintentionally compromising security, while external threats come from hackers and cybercriminals. Understanding the differences between these threats is vital for developing effective security protocols.
3. Identifying Your Organization’s Risk Profile
To protect your internal communication software, you need to identify your organization’s risk profile. This involves assessing your current security measures, evaluating potential vulnerabilities, and considering the potential impact of a security breach. The following table outlines key factors to consider when assessing your risk profile:
| Risk Factor | Low Risk | High Risk |
| Employee Training | Regular security training | Lack of security awareness |
| Software Updates | Timely updates and patches | Outdated software |
| Access Controls | Strict access controls | Lack of access controls |
By understanding these factors and assessing your organization’s risk profile, you can take proactive steps to secure your internal communication software and protect your sensitive information.
Essential Encryption Technologies for Message Security
To safeguard your internal messages, it’s crucial to understand the encryption technologies that protect them. Encryption is a critical component of secure communication, and several technologies work together to ensure your messages remain confidential.
1. End-to-End Encryption Explained
End-to-end encryption is a method of secure communication that ensures only the sender and the intended recipient can read the messages. This is achieved by encrypting the data on the sender’s device and decrypting it on the recipient’s device.
How End-to-End Encryption Protects Your Messages
End-to-end encryption protects your messages by making them unreadable to anyone except the sender and the recipient. This means that even the service provider cannot access the encrypted data.
Limitations of Encryption
While end-to-end encryption is highly secure, it’s not foolproof. Limitations include potential vulnerabilities in the implementation and the risk of losing access to your data if you forget your encryption key.
2. Transport Layer Security (TLS) and Its Importance
Transport Layer Security (TLS) is another crucial encryption technology that secures data in transit between your organization’s servers and clients. TLS ensures that data exchanged between the server and client remains encrypted and tamper-proof.
| Encryption Technology | Purpose | Key Benefits |
| End-to-End Encryption | Secure messaging between sender and recipient | Ensures confidentiality, protects against interception |
| Transport Layer Security (TLS) | Secure data exchange between servers and clients | Encrypts data in transit, prevents tampering |
| Zero-Knowledge Proof Systems | Verify data without revealing the data itself | Enhances security, maintains data privacy |
3. Zero-Knowledge Proof Systems
Zero-knowledge proof systems are cryptographic techniques that enable one party to prove that a statement is true without revealing any underlying information. This technology enhances security and maintains data privacy.
By understanding and implementing these encryption technologies, you can significantly enhance the security of your internal messages and protect your organization’s sensitive information.
Implementing Secure Internal Communication Systems
As businesses increasingly rely on digital communication, implementing secure internal communication systems has become a top priority. With the rise in cyber threats and data breaches, companies must adopt robust security measures to protect their sensitive information. A secure internal communication system is crucial for maintaining the confidentiality, integrity, and availability of business communications.
1. Key Features of Secure Messaging Platforms
When selecting a secure messaging platform, there are several key features to look for. These features are designed to ensure that your internal communications remain secure and compliant with regulatory requirements.
Authentication and Access Controls
Robust authentication mechanisms are essential for preventing unauthorized access to your messaging platform. This includes features like multi-factor authentication (MFA) and role-based access controls.
Message Retention and Deletion Policies
A secure messaging platform should allow you to implement effective message retention and deletion policies. This ensures that messages are stored for the required amount of time and are deleted when no longer needed.
Compliance Capabilities
Compliance with regulatory requirements is critical for businesses. A secure messaging platform should provide features that enable you to comply with relevant laws and regulations, such as data retention and e-discovery capabilities.
2. Top Secure Messaging Platforms for Businesses
Several secure messaging platforms are available for businesses, each with their unique features and benefits. Some of the top platforms include:
- Signal: Known for its end-to-end encryption and open-source protocol.
- Wire: Offers end-to-end encryption and secure file sharing.
- Threema: Provides secure messaging with a focus on user anonymity.
As noted by security expert Bruce Schneier, “The best way to protect your communications is to use a secure messaging app that provides end-to-end encryption.” This highlights the importance of choosing a messaging platform that prioritizes security.
3. Secure File Sharing Solutions
In addition to secure messaging, secure file sharing is also crucial for businesses. This involves using platforms that provide end-to-end encryption and access controls to ensure that sensitive files are protected. Some popular secure file sharing solutions include:
- Dropbox: Offers secure file sharing with granular access controls.
- Box: Provides secure file sharing and collaboration tools.
- pCloud: Offers end-to-end encrypted file sharing and storage.
By implementing a secure internal communication system, including a secure messaging platform and file sharing solution, businesses can significantly reduce the risk of data breaches and cyber threats.
Developing Workplace Communication Security Protocols
To safeguard your organization’s sensitive information, it’s essential to develop comprehensive workplace communication security protocols. These protocols serve as the foundation for secure team collaboration, ensuring that your team’s internal messages and data remain protected from unauthorized access.
Effective security protocols involve multiple layers of protection and require a thorough understanding of your organization’s communication vulnerabilities. By establishing clear guidelines and procedures, you can significantly reduce the risk of data breaches and cyber threats.
1. Creating a Comprehensive Secure Communication Policy
A comprehensive secure communication policy is the cornerstone of your organization’s data protection strategy. This policy should outline the procedures for internal and external communications, including the use of encryption, password management, and access controls.
- Define the scope of the policy and the roles responsible for its implementation.
- Establish guidelines for the use of company-owned and personal devices for work-related communications.
- Specify the protocols for reporting and responding to security incidents.
By having a well-defined policy in place, you can ensure that all employees understand their roles in maintaining secure team collaboration and the importance of adhering to security protocols.
2. Employee Training for Secure Team Collaboration
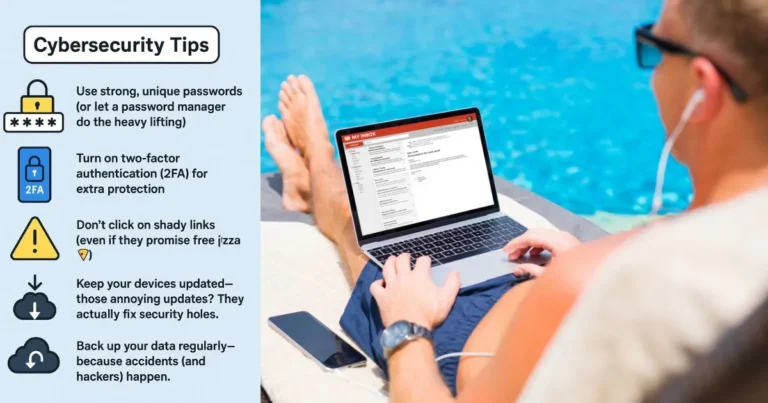
Employee training is a critical component of any security protocol. It’s essential to educate your team on the best practices for secure communication, including how to identify phishing attempts, use strong passwords, and report suspicious activity.
Regular training sessions and workshops can help reinforce these practices and ensure that your team remains vigilant in the face of evolving cyber threats. By investing in employee training, you can foster a culture of security awareness that supports secure team collaboration.
“The security of our internal communications is only as strong as the weakest link in our chain. By educating our employees on security best practices, we can significantly reduce the risk of a data breach.”
— Cybersecurity Expert
3. Monitoring, Auditing, and Compliance
Ongoing monitoring and auditing are crucial for ensuring that your security protocols remain effective. Regularly review your communication systems and practices to identify areas for improvement and detect potential security incidents.
Compliance with relevant regulations and standards, such as GDPR and HIPAA, is also essential. By staying up-to-date with the latest compliance requirements, you can ensure that your organization’s secure team collaboration practices meet the necessary standards.
Conclusion: Building a Culture of Data Privacy
As you manage the challenges of modern business communications, safeguarding your internal messages is vital to uphold trust and integrity within your organization.
By identifying vulnerabilities in your communication systems and implementing strong security measures, such as end-to-end encryption and secure file sharing, you can significantly lower the likelihood of a data breach.
Secure file sharing is crucial for protecting data privacy by ensuring that sensitive information is only accessible to authorized users.
Building a data privacy culture involves creating thorough security protocols, educating employees on secure communication techniques, and continuously monitoring and auditing your systems.
By following these steps, you can create a secure and trustworthy environment that ensures your organization’s sustained success.
FAQ – Protecting Internal Messages
What is end-to-end encryption, and how does it help in protecting internal messages?
End-to-end encryption is one of the most effective methods for protecting internal messages. It ensures that only the sender and the intended recipient can access the content. The message is encrypted on your device and remains unreadable to anyone else, including hackers or third parties.
How can I tell if my internal communication software is really protecting internal messages?
To verify that your communication tool is protecting internal messages, make sure it offers end-to-end encryption, strong authentication protocols, and access controls. Also, check whether the software adheres to data privacy laws and is trusted within the cybersecurity community.
Which features are essential in a secure messaging platform focused on protecting internal messages?
When choosing a platform for protecting internal messages, look for robust features like end-to-end encryption, authentication systems, access control options, message deletion and retention policies, and regulatory compliance tools.
How do I make sure my employees are contributing to protecting internal messages?
Start with training. Educate your team on best practices for protecting internal messages, like using secure platforms and following communication policies. Implement a clear internal communication policy and regularly monitor adherence to security standards.
What’s the role of TLS (Transport Layer Security) in protecting internal messages?
TLS is a vital technology for protecting internal messages during transmission. It encrypts the communication while it’s being sent, so even if a cybercriminal intercepts the data, they won’t be able to read it. It’s a core part of keeping sensitive info safe.
How can I securely share documents while protecting internal messages and data?
To safely share files, use a secure file-sharing service with strong encryption and user access controls. This way, you’re not only protecting internal messages but also ensuring files are only accessible to authorized team members.
What are zero-knowledge proof systems, and how do they help in protecting internal messages?
Zero-knowledge proofs allow someone to verify a statement without revealing any details behind it. In the context of protecting internal messages, they add an extra layer of trust and security, making it harder for attackers to access or manipulate sensitive information.